Robust Watermarking Using FFT and Cordic QR Techniques
Main Article Content
Abstract
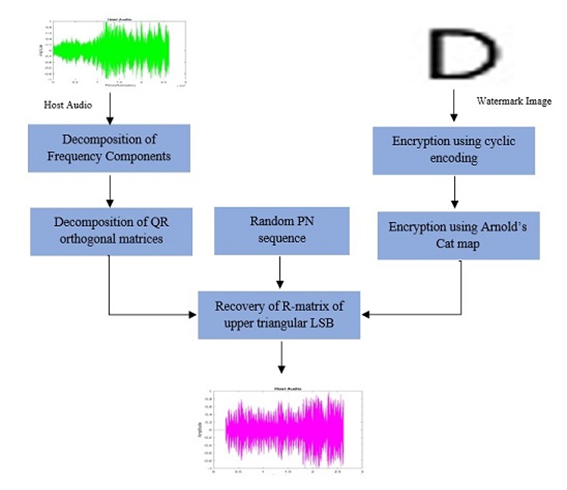
Digital media sharing and access in today’s world of the internet is very frequent for every user. The management of digital rights may come into threat easily as the accessibility of data through the internet become wide. Sharing digital information under security procedures can be easily compromised due to the various vulnerabilities floating over the internet. Existing research has been tied to protecting internet channels to ensure the safety of digital data. Researchers have investigated various encryption techniques to prevent digital rights management but certain challenges including external potential attacks cannot be avoided that may give unauthorized access to digital media. The proposed model endorsed the concept of watermarking in digital data to uplift media security and ensure digital rights management. The system provides an efficient procedure to conduct over-watermarking in digital audio signals and confirm the avoidance of ownership of the host data. The proposed technique uses a watermark picture as a signature that has been initially encrypted with Arnold's cat map and cyclic encoding before being embedded. The upper triangular R-matrix component of the energy band was then created by using the Fast Fourier transform and Cordic QR procedures to the host audio stream. Using PN random sequences, the encrypted watermarking image has been embedded in the host audio component of the R-matrix. The same procedure has been applied to extract the watermark image from the watermarked audio. The proposed model evaluates the quality of the watermarked audio and extracted watermark image. The average PSNR of the watermarked audio is found to be 37.01 dB. It has also been seen that the average PSNR, Normal cross-correlation, BER, SSMI (structure similarity index matric) value for the extracted watermark image is found to be 96.30 dB, 0.9042 units, 0.1033 units, and 0.9836 units respectively. Further, the model has been tested using various attacks to check its robustness. After applying attacks such as noising, filtering, cropping, and resampling on the watermarked audio, the watermark image has been extricated and its quality has been checked under the standard parameters. It has been found that the quality of the recovered watermark image satisfying enough to justify the digital ownership of the host audio. Hence, the proposed watermarking model attains a perfect balance between imperceptibility, payload, and robustness.
Article Details
References
Kumar, A., Rajput, S. S., & Singh, V. (2021). An Improved Approach to Secure Digital Audio Using Hybrid Decomposition Technique. In Proceedings of the International Conference on Paradigms of Computing, Communication and Data Sciences: PCCDS 2020 (pp. 361-375). Springer Singapore.
P. Zheng and Y. Zhang, "A robust image watermarking scheme in hybrid transform domains resisting to rotation attacks," Multimedia Tools and Applications, 2020.
O. P. Singh, G. Srivastava, N. Kumar and A. Singh, "Image watermarking using soft computing techniques:A comprehensive survey," Multimedia Tools and Applications, 2020.
Z. Xia, X. Wang and L. Zhang, "A Privacy-Preserving and Copy-Deterrence Content-Based Image Retrieval Scheme in Cloud Computing," IEEE Transactions on Information Forensics and Security, vol. XI, no. 11, pp. 2594 - 2608, 2016.
J. m. Zain and L. Chongmin, "Robust Image Watermarking Theories and Techniques: A Review," Journal of Applied Research and Technology, vol. XII, no. 1, pp. 122-138, 2015.
P. Pandey, S. Kumar and S. K. Singh, "A robust logo watermarking technique in divisive normalization transform domain," Multimedia Tools and Application, 2013.
R. Mehta, K. gupta and A. K. Yadav, "An adaptive framework to image watermarking based on the twin support vector regression and genetic algorithm in lifting wavelet transform domain," Multimedia Tools and Application, 2020.
R. Thanki and S. Borra, "Fragile watermarking for copyright authentication and tamper detection of medical images using compressive sensing (CS) based encryption and contourlet domain processing," Multimedia Tools and Applications, 2018.
A. Anand and A. K. Singh, "An improved DWT-SVD domain watermarking for medical information security," Computer Communication, 2020.
E. H. Rachmawanti and H. A. Santoso, "A non-blind robust and impercept watermarking using discrete cosine transform and discrete wavelet transform and discrete wavelet transform," Kinetik: Game Technology, Information System, Computer Network, Computing, Electronics, and Control Journal homepage, vol. 6, pp. 69-76, 2021.
D. Ariatmanto and F. Ernawan, "Adaptive scaling factors based on the impact of selected DCT coefficients for image watermarking," Journal of King Saud University –Computer and Information Sciences, 2020.
Suresh and R. Kishore, "A Novel and Efficient Blind Image Watermarking In Transform Domain," Procedia Computer Science, vol. 167, pp. 1505-1514, 2020.
J. Wang and W. Wen, "A novel attention-guided JND Model for improving robust image watermarking," Multimedia Tools and Applications, vol. 79, 2020.
Baser, P. ., Jatinderkumar R. Saini, & Baser, N. . (2023). Gold Commodity Price Prediction Using Tree-based Prediction Models. International Journal of Intelligent Systems and Applications in Engineering, 11(1s), 90–96. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2481
F. N. Al-Wesabi, K. Mahmood and N. NEMRI, "A zero watermarking approach for content authentication and tampering detection of Arabic text based on fourth level order and word mechanism of Markov model," Journal of Information Security and Applications, 2020.
J. Y. Li and C. Z. Zhang, "Blind watermarking scheme based on Schur decomposition and non-subsampled contourlet transform," Multimedia Tools and Applications, p. 30007–30021, 2020.
A. Dwivedi, A. Kumar, M. K. Dutta, R. Burget, and V. Myska, "An Efficient and Robust Zero-Bit Watermarking Technique for Biometric Image Protection," 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 2019, pp. 236-240, doi: 10.1109/TSP.2019.8768881.
A. Kumar, A. Dwivedi, and M. K. Dutta, "A Zero watermarking Approach for Biometric Image Security," 2020 International Conference on Contemporary Computing and Applications (IC3A), Lucknow, India, 2020, pp. 53-58, doi: 10.1109/IC3A48958.2020.233268.
Ólafur, J., Virtanen, M., Vries, J. de, Müller, T., & Müller, D. Data-Driven Decision Making in Engineering Management: A Machine Learning Framework. Kuwait Journal of Machine Learning, 1(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/108
A. Singh, A. Kumar and M. K. Dutta, "DWT, DCT and PBFO based Approach for Biometric Image Security," 2020 International Conference on Contemporary Computing and Applications (IC3A), Lucknow, India, 2020, pp. 298-303, doi: 10.1109/IC3A48958.2020.233317.
Kumar, A., Singh, A., Prakash, S., & Singh, V. (2021). A novel approach towards audio watermarking using FFT and CORDIC?Based QR Decomposition. AI and IoT?Based Intelligent Automation in Robotics, 323-338.
Singh, A., Kumar, A., Dutta, M. K., Travieso-González, C., & Esteban-Hernández, L. (2020, January). Perspective Approach for Security of Biometric Image. In Proceedings of the 3rd International Conference on Applications of Intelligent Systems (pp. 1-7).