SRP-HEE: A Modified Stateless Routing Protocol based on Homomorphic Energy based Encryption for Wireless Sensor Network
Main Article Content
Abstract
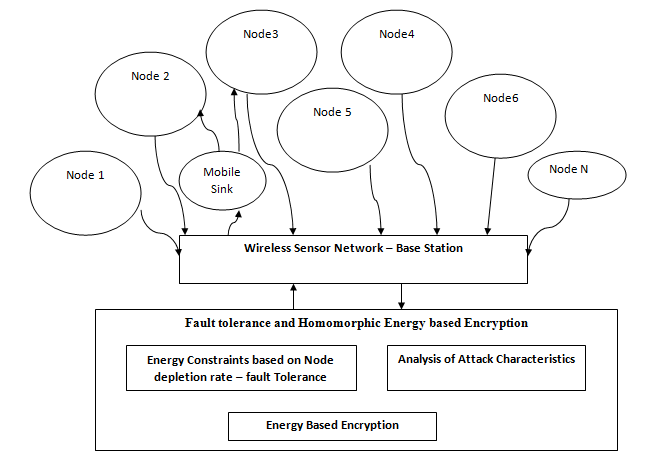
Due to the wireless nature, the sensors node data are prone to location privacy of source and classification of the packet by unauthorized parties. Data encryption is one of the most effective ways to thwart unauthorized access to the data and trace information. Traditional wireless network security solutions are not viable for WSNs In this paper, a novel distributed forward aware factor based heuristics towards generating greedy routing using stateless routing is SRP-HEE for wireless sensor network. The model employs the homomorphic Energy based encryption technique. Energy based Encryption model is devoted as homomorphic mechanism due to their less computational complexity. Additionally, privacy constraint becoming a critical issue in the wireless sensor networks (WSNs) because sensor nodes are generally prone to attacks which deplete energy quickly as it is exposed to mobile sink frequently for data transmission. Through inclusion of the Forward aware factor on the Greedy routing strategies, it is possible to eliminate the attacking node which is depleting the energy of the source node. Heuristic conditions are used for optimizing the sampling rate and battery level for tackling the battery capacity constraints of the wireless sensor nodes. The Node characteristics of the propagating node have been analysed utilizing kalman filter and linear regression. The cooperative caching of the network information will enable to handle the fault condition by changing the privacy level of the network. The Simulation results demonstrate that SRP-HEE model outperforms existing technique on basis of Latency, Packet Delivery Ratio, Network Overhead, and Energy Utilization of nodes.
Article Details
References
C. Ma et al., “Coverage overlapping problems in applications of IEEE 802.15.4 wireless sensor networks” in Proc. IEEE Wireless Communications and Networking Conference (WCNC): Services Applications, vol. 4369, 2013, pp. 4364-4369 [doi:10.1109/WCNC.2013.6555280].
Liang Cheng Shiu, Chao Yang Lee, and Chu Sing Yang, “The divide-and-conquer deployment algorithm based on triangles for wireless sensor networks,” IEEE Sensors J., vol. 11, no. 3, pp. 781-790, Mar. 2011 [doi:10.1109/JSEN.2010.2059006].
Ting-Yu Lin, Member, IEEE , Hendro Agus Santoso, and Kun-Ru Wu, ” Global Sensor Deployment and Local Coverage-Aware Recovery Schemes for Smart Environments in IEEE, Transactions on Mobile Computing, vol. 14, no. 7, Jul., 2015,pp-1382-1396. [doi:10.1109/TMC.2014.2353613].
Seapahn Megerian, Farinaz Koushanfar, Miodrag Potkonjak, and Mani B. Srivastava, Senior Member, IEEE, “Worst and best-case coverage in sensor networks,” IIEEE TRANSACTIONS ON MOBILE COMPUTING, vol. 4, no. 1, pp. 84-92, Jan./Feb. 2005 [doi:10.1109/TMC.2005.15].
Amin Vahdat and David Becker, Epidemic Routing for Partially Connected Ad Hoc Networks Technical Report CS-200006. Duke Univ., 2000.
D. Tian and N. D. Georganas, “A Coverage-preserving node scheduling scheme for large wireless sensor networks” in Proceedings of the1st ACM international workshop on Wireless sensor networks and applications., Sept. 2002, pp. 32-41 [doi:10.1145/570738.570744].
Ze Li, Haiying Shen, “A QoS-Oriented Distributed Routing Protocol for Hybrid Wireless Networks" in IEEE TRANSACTIONS ON MOBILE COMPUTING.,IEEE TRANSACTIONS ON MOBILE COMPUTING, vol. 13, pp. 693-708, Mar. 2014 [doi:10.1109/TMC.2012.258].
Mahesh Vaidya; Ekjot Singh Walia; Aditya Gupta, “’ IEEE International Conference on Advances in Engineering & Technology Research (ICAETR - 2014) [doi: 10.1109/ICAETR.2014.7012798]
Alejandro Proan˜o and Loukas Lazos, " Packet-Hiding Methods for Preventing Selective Jamming Attacks",IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING, VOL. 9, NO. 1, pp.101-114, JANUARY/FEBRUARY 2012, [doi:10.1109/TDSC.2011.41].
R.L. Rivest, A.Shamir and D.A.Wagner, ‘Time-Lock Puzzles and Timed-Release Crypto,’ Technical Report. Massachusetts Inst. of Technology, 1996.
DOUGLAS S. J. DE COUTO, DANIEL AGUAYO, JOHN BICKET and ROBERT MORRIS, “A High-Throughput Path Metric for Multi-Hop Wireless Routing” in Wireless Networks Springer Science + Business Media, Inc. Manufactured in The Netherlands., vol 11, no. 4, Jul. 2005, pp. 419-434, [doi:10.1007/s11276-005-1766-z].
Sungjin Lee & Sanghoon Lee, “Optimal transmission methodology for QoS provision of multi-hop cellular network,” Wireless Netw., vol. 16, no. 5, pp. 1313-1327, 2010 [doi:10.1007/s11276-009-0205-y].
Veena Safdar, Faisal Bashir, Zara Hamid, Hammad Afzal and Jae Young Pyun, “A hybrid routing protocol for wireless sensor networks with mobile sinks” in Proc. 7th Int. Symp. Wireless Pervasive Comput., 2012, pp. 1-5 [doi:10.1109/ISWPC.2012.6263665].
Ioannis Chatzigiannakis, Athanasios Kinalis and Sotiris Nikoletseas , “Efficient data propagation strategies in wireless sensor networks using a single mobile sink”, Computer Communications, vol. 31, no. 5, pp. 896914, 2008.[doi:10.1016/j.comcom.2007.12.011].
Tian He, John A Stankovic, Chenyang Lu and Tarek Abdelzaher, “SPEED: A Stateless Protocol for Real-Time Communication in Sensor Networks” in Proc. 23rd Int. Conf. Distributed Computing Systems, Jun 2003,Providence, RI, USA, .[doi:10.1109/ICDCS.2003.1203451].
Amir Nader Shahbaz, Hamid Barati & Ali Barati, "Multipath routing through the firefly algorithm and fuzzy logic in wireless sensor networks,” Peer-to-Peer Networking and Appl., vol. 14, no. 2, pp. 541-558, 2021 [doi:10.1007/s12083-020-01004-2].
Zahra Hajipour & Hamid Barati, “EELRP: Energy efficient layered routing protocol in wireless sensor networks,” Computing, vol. 103, no. 12, pp. 2789-2809, 2021 [doi:10.1007/s00607-021-00996-w].
Isaac Sajan R and Jasper J, “A secure routing scheme to mitigate attack in wireless adhoc sensor network,” Computers & Security, vol. 103, p. 102197, 2021 [doi:10.1016/j.cose.2021.102197].
Nitin Mittal, Simrandeep Singh, Urvinder Singh and Rohit Salgotra, “Trust-aware energy-efficient stable clustering approach using fuzzy type-2 Cuckoo search optimization algorithm for wireless sensor networks,” Wireless Networks, vol. 27, no. 1, pp. 151-174, 2021 [doi:10.1007/s11276-020-02438-5].
Weidong Fang, Wuxiong Zhang, Wei Yang, Zhannan Li, Weiwei Gao and Yinxuan Yang, “Trust management-based and energy efficient hierarchical routing protocol in wireless sensor networks,” Digital Communications and Networks, vol. 7, no. 4, pp. 470-478, 2021 [doi:10.1016/j.dcan.2021.03.005].
Ali Shahidinejad and Saeid Barshandeh, “Sink selection and clustering using fuzzy-based controller for wireless sensor networks,” Int. J. of Communication Systems, vol. 33, no. 15, p. e4557, 2020 [doi:10.1002/dac.4557].
GULZAR MEHMOOD1, MUHAMMAD ZAHID KHAN, ABDUL WAHEED, MAHDI ZAREEI and EHAB MAHMOUD MOHAMED, “A trust-based energy-efficient and reliable communication scheme (trust-based ERCS) for remote patient monitoring in wireless body area networks,” IEEE Access, vol. 8, pp. 131397-131413, 2020 [doi:10.1109/ACCESS.2020.3007405].
Elham Hasheminejad & Hamid Barati, “A reliable tree-based data aggregation method in wireless sensor networks,” Peer-to-Peer Networking and Applications, vol. 14, no. 2, pp. 873-887, 2021 [doi:10.1007/s12083-020-01025-x].
Maryam Naghibi & Hamid Barati, “SHSDA: Secure hybrid structure data aggregation method in wireless sensor networks,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, pp. 10769–10788, 2021.[doi: 10.1007/s12652-020-02751-z].
Sedigheh Sadat Sharifi and Hamid Barati, “A method for routing and data aggregating in cluster-based wireless sensor networks,” International Journal of Communication Systems, vol. 34, no. 7, p. e4754, 2021 [doi:10.1002/dac.4754].