Sinkhole Detection in IOT using Elliptic Curve Digital Signature
Main Article Content
Abstract
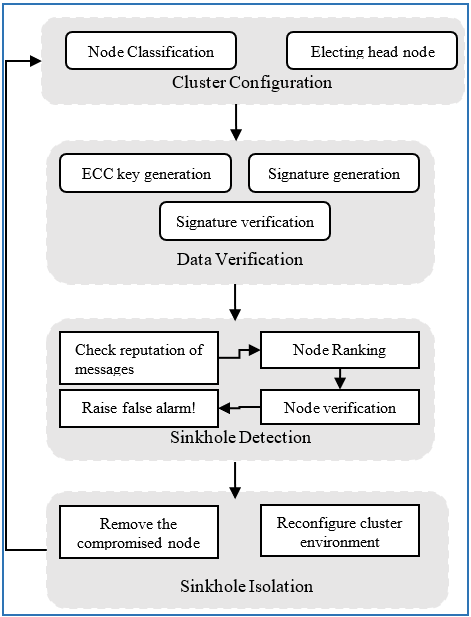
A variety of smart applications, including homes, transportation, health, and robots in industries, are starting to gain interest due to the fast expansion of Internet of Things (IoT). Smart devices are made up of sensors and actuators that actively involved in monitoring, prediction, security, and information sharing in the IoT ecosystem. These state-of-the-art (SOTA) technologies enable people to monitor and manage their unified milieu in real-time. IoT devices are nevertheless regularly used in hostile situations, where attackers try to grab and penetrate them to take over the entire network. Due to the possibility of selective forwarding, sinkhole, blackhole, and wormhole attacks on IoT networks is a serious security risk. This research offers an effective method using a digital signature to detect and mitigate sinkhole attacks on IoT networks to resolve this problem. By doing a thorough security study of this suggested system, it shows how safe it is and how resistant it is to secure sinkhole attack detection. In this study, elliptic curve digital signature algorithm is used along with the node ranker to detect the sinkhole attack in IoT environment. According to the performance analysis and experimental findings compared to other research, the suggested system offers good detection accuracy and greatly lowers the overhead associated with computing, communication, and storage.
Article Details
References
Y. A. Qadri, A. Nauman, Y. B. Zikria, A. V. Vasilakos, S. W. Kim, “The future of healthcare internet of things: a survey of emerging technologies,” IEEE Communications Surveys & Tutorials, 22 (2), pp. 1121–1167, 2020.
Awajan, A. (February 2023). “A Novel Deep Learning-Based Intrusion Detection System for IoT Networks.” Computers, vol. 12. Available: https://doi.org/10.3390/computers12020034.
Khizar Hameeda, Saurabh Garga, Muhammad Bilal Amina, Byeong Kanga, Abid Khanb. “A Context-Aware Information-Based Clone Node Attack Detection Scheme in Internet of Things”. Journal of Network and Computer Applications, vol. 197, January 2022
Zaminkar, M. and Fotohi, R., SoS-RPL: securing internet of things against sinkhole attack using RPL protocol-based node rating and ranking mechanism, Wireless Personal Communications, vol. 114(2), pp.1287-1312, 2020.
5. C. Cervantes, D. Poplade, M. Nogueira and A. Santos, "Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things," in Proc. 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), pp. 606-611, 2015.
Ga Hyeon An, Tae Ho Cho. “Improving Sinkhole Attack Detection Rate through Knowledge-Based Specification Rule for a Sinkhole Attack Intrusion Detection Technique of IoT”. International Journal of Computer Networks and Applications (IJCNA), vol. 9, 2022.
S. Alexander Suresh SDB and Dr.Jemima Priyadarsini, ETSET: “Enhanced Tiny Symmetric Encryption Techniques to Secure Data Transmission among IoT Devices”, Turkish Journal of Computer and Mathematics Education, vol.12 No.10: pp. 1094-1099, 2021.
C. Linda Hepsiba, Dr. R. Jemima Priyadarsini, Dr. S. Titus, “A Comprehensive Study on Routing Attacks with Countermeasures in Internet of Things”, Solid State Technology, vol. 63 No. 4: 7993-7999, 2020.
Jeethu Mathew, Dr. R. Jemima Priyadarsini, “A Review on DoS Attacks in IoT,” Solid State Technology, vol. 63 No. 4: pp. 8000-8009, 2020.
Mr. S. Alexander Suresh, Dr. R. Jemima Priyadarsini, “A Comprehensive Study on Sybil Attacks and Its Defence Mechanisms in Internet of Things”, Solid State Technology, vol. 63 No. 4: pp. 7966 – 7974, 2020.
J. Rani, A. Dhingra and V. Sindhu, “A Detailed Review of the IoT with Detection of Sinkhole Attacks in RPL based network,” in Proc. International Conference on Communication, Computing and Internet of Things (IC3IoT), Chennai, India, pp. 1-6, 2022.
Maung, Tay Zar Bhone, and Lunchakorn Wuttisittikulkij. "A Comprehensive Survey of Sinkhole Attack in Routing Protocol for Low-Power and Lossy Networks for IoT Devices." in Proc. The 14th Regional Conference on Electrical and Electronics Engineering (RC-EEE 2021), 2022.
Ahmad Mujtaba, Dr. Ammar Rafiq, Salal Amjad, Asim Mubarik, Muhammad Usman Younas. “Enhancement of accuracy of the Rank Inconsistency Detection Algorithm”, Pakistan journal of engineering and applied sciences, vol. 30, Jan 2022.
Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, “A. Internet of Things: Security and Solutions, Survey”, Sensors, vol. 22, 2022.
Takieldeen, FK Ali E., and Fahmi Khalifa. “Authentication and Encryption of IoT Devices Based on Elliptic Curves: A survey.” Journal of Intelligent Systems and Internet of Things (JISIoT), vol. 5 2021.
Szymoniak, S.; Kesar, S. “Key Agreement and Authentication Protocols in the Internet of Things: A Survey”. Appl. Sci., vol. 13, 2023.
Kaur, Jaspreet, and Gagandeep Singh. “A Blockchain-Based Machine Learning Intrusion Detection System for Internet of Things.” Principles and Practice of Blockchains. Springer, Cham, pp. 119-134, 2023.
Zubaydi, H.D.; Varga, P.; Molnár, S. “Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review.” Sensors, vol. 23, 2023.
Bandarupalli Rakesh and Parveen Sultana H. “Novel Authentication and Secure Trust based RPL Routing in Mobile sink supported Internet of Things,” Cyber-Physical Systems, vol. 9, pp. 43-76, 2023.
S. Velliangiri, Iwin Thanakumar Joseph, Shanthini Pandiaraj, P. Leela Jancy and Ch. Madhubabu. “An enhanced security framework for IoT environment using Jaya optimisation-based genetic algorithm.” International Journal of Internet Technology and Secured Transactions, vol. 13, no. 1. November 2022.
Mohsen Sheibani, Behrang Barekatain, Erfan Arvan. “A lightweight distributed detection algorithm for DDAO attack on RPL routing protocol in Internet of Things.” Pervasive and Mobile Computing, vol. 80, February 2022.